News
The complete list of Q2 2024 releases and updates on HTB Enterprise Platform
Responding to the feedback we’ve received from our 2.9 million community of cybersecurity professionals, we’re excited to share the new Hack The Box updates released over the past 3 months.

katemous,
Jul 16
2024
Explore the latest updates on the HTB Enterprise Platform, our all-in-one cloud-based solution to optimize workforce development and organizational resilience.
These enhancements streamline your team's upskilling process while providing clear insights into every aspect of your team's cyber performance.
Watch our latest video for a full walkthrough of the new product highlights!
General improvements across the platform
Dedicated Labs Spaces for laser-focused skill development
In April we introduced Dedicated Labs Spaces, a new feature that levels up cohort-based skills development.
Spaces provide a structured approach to organizing team members and scenarios within the HTB Enterprise Platform. They facilitate personalized learning experiences and efficient management within cybersecurity teams, simplifying practices such as:
-
Benchmarking and skill gap analysis: Creating tailored Spaces for testing and refining specific skill sets using hands-on exercises from HTB’s library of over 1,000 offensive and defensive labs.
-
Technical onboarding: Accelerating onboarding by using Spaces to immerse new employees in real-world threats, enhancing skill retention, and reducing training time.
-
Recruitment and candidate assessment: Optimizing the hiring process with practical simulations that assess candidates' abilities, saving time and resources while ensuring the right fit.
NIST | NICE content categorization for reporting and skills progression
Cybersecurity training often falls short of addressing the real-world skills that organizations need, leaving teams underprepared.
The NIST | NICE framework bridges this gap by outlining the essential Knowledge, Skills, Abilities, and Tasks (KSATs) required for cybersecurity roles. This ensures that training enhances team performance and aligns with industry standards.
By integrating the NIST | NICE framework into the HTB Enterprise Platform, we’ve categorized all Academy Modules according to these standards.
Managers can now develop skill-focused training by adding tailored content to their Lab, using any keyword, NICE skill code, task, knowledge area, or work role.
Additionally, security leaders can leverage the NIST | NICE framework on the Reporting page to assess team performance, identify skill gaps, and pave the way for strategic workforce development initiatives.
Advanced search functionality for threat-aligned lab selection
Managers can now easily search for Machines within Dedicated Labs using all available tags, allowing broader searches linked to real-world skills and CVEs.
This enables faster response times by tailoring a team’s skills development plan to emerging threats.
See how to pick a CVE Machine in just a few clicks.
Academy for Business
6 offensive courses added to Academy for Business

We’ve introduced six (6) new offensive courses in Academy for Business, designed to empower teams with the essential knowledge and skills to thrive in cybersecurity.
Let’s summarise what your team will learn by completing our new courses:
-
Introduction to Windows Evasion Techniques: Understand Windows Defender antivirus mechanisms, apply common evasion techniques, and analyze the impact of evasion.
-
DACL Attacks II: Learn to detect and mitigate DACL-based attacks, and develop skills in safeguarding and compromising Active Directory networks.
-
Attacking Authentication Mechanisms: Identify common authentication mechanisms such as JWT, OAuth, and SAML. As well as vulnerabilities resulting from improper use of standardized access controls.
-
Active Directory Trust Attacks: Master Active Directory by learning identity management, attacking domain trusts, mitigating risks, and navigating advanced pentesting techniques.
-
Intro to C2 Operations with Silver: Learn how attackers gain initial access and escalate to full forest compromise using Sliver C2 and other powerful open-source tools.
-
Introduction to Binary Fuzzing: Uncover hidden bugs and security vulnerabilities lurking in code blocks.
These new Academy Modules provide comprehensive knowledge that covers everything from evasion techniques to advanced Active Directory attacks, to equip teams with the necessary skills to safeguard organizations and uphold stringent security measures for IT environments.
Dedicated Labs
80 offensive and defensive scenarios added on Dedicated Labs

In the second quarter of 2024, we set a new record by releasing eighty (80) offensive and defensive scenarios in Dedicated Labs. This demonstrates our commitment to delivering cutting-edge training that equips teams with the skills to tackle today’s and tomorrow’s cybersecurity challenges.
These scenarios cover a wide range of cybersecurity domains, addressing everything from CVE exploitation and Active Directory to Artificial Intelligence and Machine Learning vulnerabilities.
Among these releases, we’ve introduced eight (8) new exclusive Machines, offering unique training opportunities across critical domains, including Linux vulnerabilities, Windows exploitation, Active Directory, and Machine Learning attacks.
Operation Shield Wall: A series of labs simulating state-side cybercrime

Operation Shield Wall features realistic scenarios simulating strategies for responding to large-scale cybersecurity incidents affecting critical infrastructure.
This themed series of hands-on labs offers a comprehensive opportunity to understand offensive strategies, improve incident response, and enhance cyber threat intelligence operations (CTI), ultimately strengthening any organization's security posture.
Key learning outcomes include:
-
Detect and investigate Wi-Fi compromises.
-
Uncover and analyze hidden data in mobile forensics.
-
Execute offensive operations on C2 servers.
-
Perform comprehensive network compromise sweeps.
-
Master SMTP, ransomware site defacement, and Jinja2 injections.
-
Reverse-engineer encryption methods and spot anti-reversing tactics.
Second Real Case Sherlock release in collaboration with top MSSPs

Real Case Sherlocks on the HTB Enterprise Platform bring unparalleled realism to cybersecurity training by replicating real-world breach scenarios shared by top Managed Security Service Providers (MSSPs).
These scenarios, like the newly released Pulse, allow teams to engage in genuine incident response situations using the exact tactics, techniques, and procedures (TTPs) employed by real attackers.
In Pulse, teams act as DFIR consultants, investigating the compromise of a corporate environment using advanced tools like HELK. Pulse allows teams to practice and learn:
-
Risks associated with the compromise of edge devices.
-
TA tool sets used to carry out objectives.
-
Windows & Web Access Log analysis utilizing SIEM technology.
Detect and mitigate critical Active Directory vulnerabilities

Downtime from Active Directory attacks can cost enterprises about $300,000 per hour. With Active Directory being a prime target for attackers, swift detection and response are essential to protect your IT infrastructure.
Our new Active Directory Series addresses these issues by offering hands-on experience with key attacks and misconfigurations, including:
Guidance for completing Web Challenges
Our step-by-step write-ups for Web Challenges, now available on the HTB Enterprise Platform, are designed to accelerate learning for cybersecurity teams.
Managers can leverage these write-ups to enhance support for their teams. When team members encounter difficulties, managers can use these detailed guides to provide targeted assistance, helping them overcome obstacles more quickly and stay on track.
For users, these write-ups offer comprehensive instructions and real-world context, leading to more efficient completion of Challenges, significantly speeding up their learning process.
Professional Labs
Tackle ICS security challenges with new lab scenario: Alchemy

Compromise a simulated industrial production facility in the new Alchemy lab, stepping into an ICS environment crafted with the support of Dragos, a leading ICS/OT cybersecurity technology and solution provider!
Alchemy is a Professional Lab scenario created to take cybersecurity teams through a series of security challenges that cross 9 Machines, 7 PLCs, and 21 flags to complete.
Representing an integrated network of IT and Operational Technology (OT) environments, Alchemy is dedicated to challenging member’s skills and familiarity with:
-
ICS security fundamentals (interact and interpret protocols).
-
ICS network segmentation.
-
Active Directory enumeration in IT and OT networks.
-
Lateral movement, tunneling, pivoting, and privilege escalation.
-
Common attacking techniques against Programmable Logic Controllers (PLCs) and Human Machine Interfaces (HMIs).
Active Directory enumeration with a new lab scenario: XEN

We introduced XEN, a new Professional Lab scenario tailored to enhance your team’s skills in enumeration, breakout, lateral movement, and privilege escalation within an Active Directory environment.
XEN simulates a security assessment for Humongous Retail, a company facing increased scrutiny after recent security breaches. This scenario challenges cyber teams to gain access to the internal network, escalate privileges, and ultimately compromise the domain, all while collecting valuable flags.
But XEN offers more than just practical experience. It ensures that Red Teams not only practice essential techniques but also deepen their understanding of enterprise network security.
XEN comes with all business-exclusive features such as official write-ups, Restore Point, and MITRE ATT&CK mapping.
Stay tuned! Upcoming scenarios will further enrich the Professional Labs library, bringing even more advanced challenges and learning opportunities to sharpen any team’s expertise.
Updates to Genesis and Breakpoint scenarios

We’re dedicated to keeping our content fresh and up-to-date with industry standards and threats. That’s why we released major updates on both Genesis and Breakpoint to enhance your team’s training experience.
Breakpoint now includes the latest Windows and Linux updates, refreshed Defender signatures, renewed SFBS certificates, and fixes for previous issues. Additionally, we've set up vmtools for maintenance and auditd for enhanced logging.
Genesis features the latest Windows updates, upgraded NIX Machines, and corrected web page comments.
Talent Search
Efficient tracking and management of reach-out requests
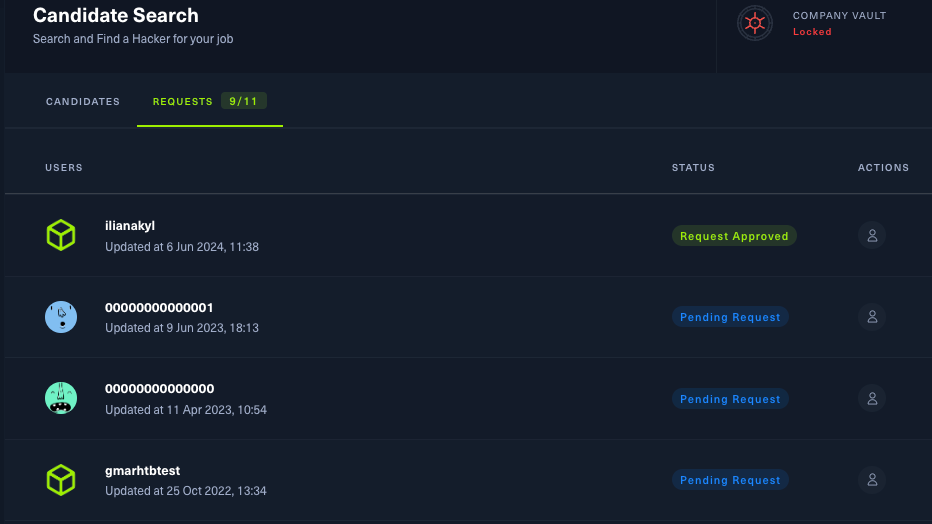
Managers can easily view the most recent updates in Candidate Search and will receive email notifications when a candidate responds positively.
This aims to make the hiring process even smoother, we’ve introduced a new feature that ensures no communication is lost. Every reach-out request is now seamlessly tracked and managed.
With Talent Search, organizations can tap into a global talent pool of over 500,000+ cybersecurity professionals with validated skills.
Capture The Flag
Streamlined CTF experience with the new CTF dashboard
CTFs are ideal for benchmarking, gap analysis, and boosting team collaboration, all while giving managers valuable insights into their team's skills.
To streamline this process, we've introduced a detailed CTF dashboard, an all-in-one hub where managers can:
-
Track team progress and performance.
-
Stay informed about upcoming, ongoing, and past events.
-
Manage events.
The dashboard functions as a strategic tool, enabling administrators to assess past performances and devise more effective plans for future challenges.
Configuration of CTF event Challenges
We’ve expanded our event management capabilities, helping managers better assess and benchmark teams and individuals while driving growth and skill development.
Managers can configure CTF events by adding or removing Challenges from a library of over 100 options, whether using a pre-made pack or creating an event from scratch.
Each Challenge comes with detailed information, including objectives, categories, average solving time, and difficulty levels, enabling managers to modify their list of Challenges to their team's skill level and goals.
Academy recommendations for CTF Challenges
CTF Academy recommendations provide guidance before, during, and after a CTF event to enhance learning, bridge HTB Academy and CTF content, and reinforce knowledge through practical and theoretical training.
Event managers can now easily identify relevant Academy Modules to their chosen CTF Challenges, guiding participants toward further skill development.
New CTF event packs for junior cybersecurity professionals
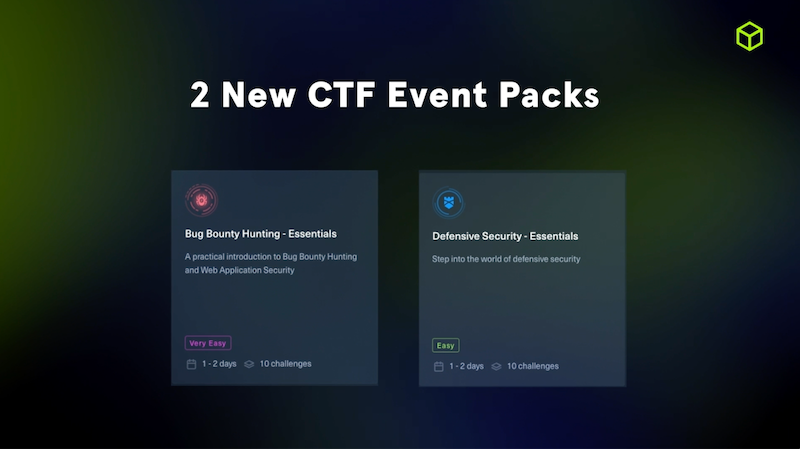
We've added two (2) new CTF event packs for junior cybersecurity professionals, providing a well-rounded approach to mastering offensive and defensive skills.
Bug Bounty Hunting - Essentials:
-
Focuses on exploiting known CVEs, directory fuzzing, and XSS vulnerabilities.
-
Contains ten (10) Challenges for assessing and developing junior Web Application Penetration Testers and Engineers.
-
Aligns with the Academy Bug Bounty Hunter job-role path, covering 75% of the recommended Modules.
Defensive Security - Essentials:
-
Builds core skills in incident response and malware analysis.
-
Includes (10) new Challenges for hands-on experience with defensive security tools and techniques.
-
Aligns with the Academy SOC Analyst job-role path, enhancing expertise in analyzing malicious files, network traffic, and memory dumps.
Fair and competitive CTF playing with Flag Rotation

We’ve introduced Flag Rotation for Challenges, a new feature designed to enhance fairness and competition in CTF events.
This new feature generates unique flags for each team upon each docker deployment, adding an extra layer of anti-cheating measures, and ensuring everyone gets a fair and competitive playing field on the HTB CTF platform.
Is your team ready to deal with the latest vulnerabilities?
Hack The Box provides a wide range of scenarios to keep your team’s skills sharp and up-to-date. Organizations like Google, Toyota, NVISO, and RS2 are already using the platform to stay ahead of threats with hands-on skills and a platform for acquiring, retaining, and developing top cyber talent.
-
Risk mitigation: Timely content offers training on the latest CVEs in real-world environments, reducing risk and exposure to these vulnerabilities.
-
Employee retention: Cybersecurity teams that are offered upskilling opportunities are far more engaged and less likely to burn out.
-
Performance benchmarking: Conduct CTFs and gap analysis to identify weaknesses in your security posture.
-
Tailored training to industry standards: HTB content is mapped to MITRE ATT&CK and NIST NICE frameworks so you can assess your cyber preparedness in different areas.
-
Boost organizational awareness: HTB can assess cyber readiness and performance company-wide with effective practices like tabletop exercises (TTXs) or nearly practical assessments designed for security staff and non-technical teams.
 Contents
Contents
- General improvements across the platform
- Academy for Business
- Dedicated Labs
- 80 offensive and defensive scenarios added on Dedicated Labs
- Operation Shield Wall: A series of labs simulating state-side cybercrime
- Second Real Case Sherlock release in collaboration with top MSSPs
- Detect and mitigate critical Active Directory vulnerabilities
- Guidance for completing Web Challenges
- Professional Labs
- Talent Search
- Capture The Flag
- Is your team ready to deal with the latest vulnerabilities?












