Red Teaming
8 Powerful Kerberos attacks (that analysts hate)
Discover the most common Kerberos attacks that every red teamer should know (and analysts fear), and learn how to execute them with real-world examples.

Dimitris,
Feb 06
2024

This post is based on the Hack The Box (HTB) Academy module (or course) on Kerberos Attacks. The module provides an in-depth study of the Kerberos protocol and its authentication process within an Active Directory network
You can learn more by browsing the catalog of free or advanced cybersecurity courses on the HTB Academy!
What is Kerberos?
Kerberos is a protocol that allows users to authenticate on the network and then access services.
When a user logs into their PC, Kerberos is used to authenticate them. It is used whenever a user wants to access a service on the network.
Thanks to Kerberos, a user doesn't need to type their password in constantly, and the server won't need to know every user's password. This is an example of centralized authentication.

Kerberos is a stateless authentication protocol based on tickets. It effectively separates a user's credentials from their requests to resources, ensuring their password is not transmitted over the network.
Is Kerberos a vulnerable authentication protocol?
In this post, we’re focusing on how to attack and infiltrate Kerberos authentification, which may lead you to believe that it’s a weak protocol. However, before Kerberos, authentication resulted in a user's hash stored within memory upon authentication.
If a target machine was compromised and the hash was stolen, the attacker could access anything that the user account had access to via a Pass-The-Hash attack.
With Kerberos authentication, credentials must be specific for every machine they want to access because there is no password. This means that the attacker is limited to the resources that the victim user authenticated against.
Kerberos is considered one of the most secure and robust authentication mechanisms out there. Although no security measure is completely invulnerable, and Kerberos is no exception.
Learn Kerberos attacks with Academy

-
Interactive module on the most common Kerberos attacks: roasting, delegation, and ticket abuse.
-
Learn how to harden, mitigate, and detect Kerberos attacks, boosting your security knowledge base.
-
Finish the course with a practical hands-on skills assessment to test your newly developed skills.
Note💡: Read our detailed (and visual) Kerberos authentication guide for a friendly intro to the world of Kerberos.
8 common Kerberos attacks explained

Roasting attacks
There are two main forms of roasting attacks: AS-REQ Roasting & Kerberoasting.
1. AS-REQ Roasting
AS-REQ Roasting is possible when Kerberos pre-authentication is not configured. This allows anyone to request authentication data for a user. In return, the KDC would provide an AS-REP message.
Since part of that message is encrypted using the user’s password, it is possible to perform an offline brute-force attack to try and retrieve the user's password.
The only information an attacker requires is the username they want to attack, which can also be found using other enumeration techniques.
If an account has pre-authentication disabled, an attacker can obtain an encrypted Ticket Granting Ticket (TGT) for the affected account without any prior authentication. These tickets are vulnerable to offline password attacks using a tool like Hashcat or John the Ripper.
So, in a nutshell, it's possible to obtain the TGT for any account that has the "Do not require Kerberos preauthentication" setting enabled.
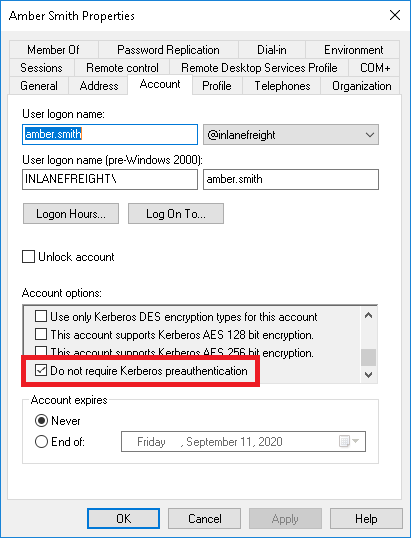
2. Kerberoasting
Kerberoasting is an attack against service accounts that allows an attacker to perform an offline password-cracking attack against the Active Directory account associated with the service.
It is similar to AS-REQ Roasting but does require prior authentication to the domain. In other words, we need a valid domain user account and password (even the lowest privileged) or a SYSTEM (or low privileged domain account) shell on a domain-joined machine to perform the attack.
Delegation attacks
Kerberos Delegation allows a service to impersonate a user to access another resource. Authentication is delegated, and the final resource responds to the service as if it had the first user's rights.
There are different types of delegation, each with weaknesses that may allow an attacker to impersonate users to leverage other services.
3. Unconstrained delegation
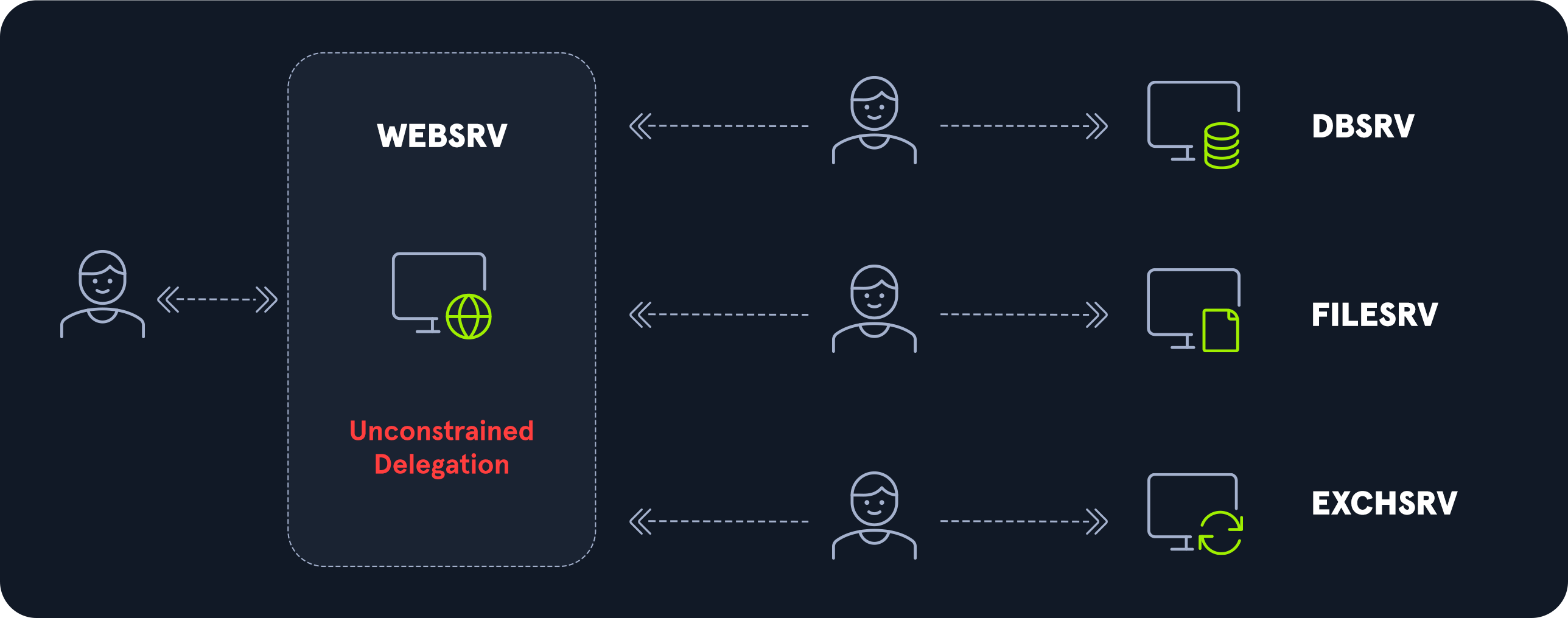
Unconstrained delegation allows a service to impersonate a user when accessing any other service. This is a very dangerous privilege, therefore, not any user can grant it.
For an account to have an unconstrained delegation, on the “Delegation” tab of the account, the “trust this computer for delegation to any service (Kerberos only)” option must be selected.
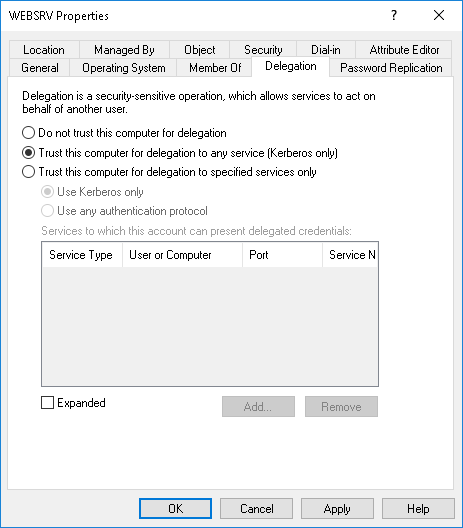
Only an administrator or a privileged user to whom these privileges have been explicitly given can set this option to other accounts. More specifically, it is necessary to have the SeEnableDelegationPrivilege privilege to perform this action. A service account cannot modify itself to add this option.
👉 Unlock the secrets to fortifying Active Directory with our practical Active Directory hardening checklist.
4. Constrained delegation
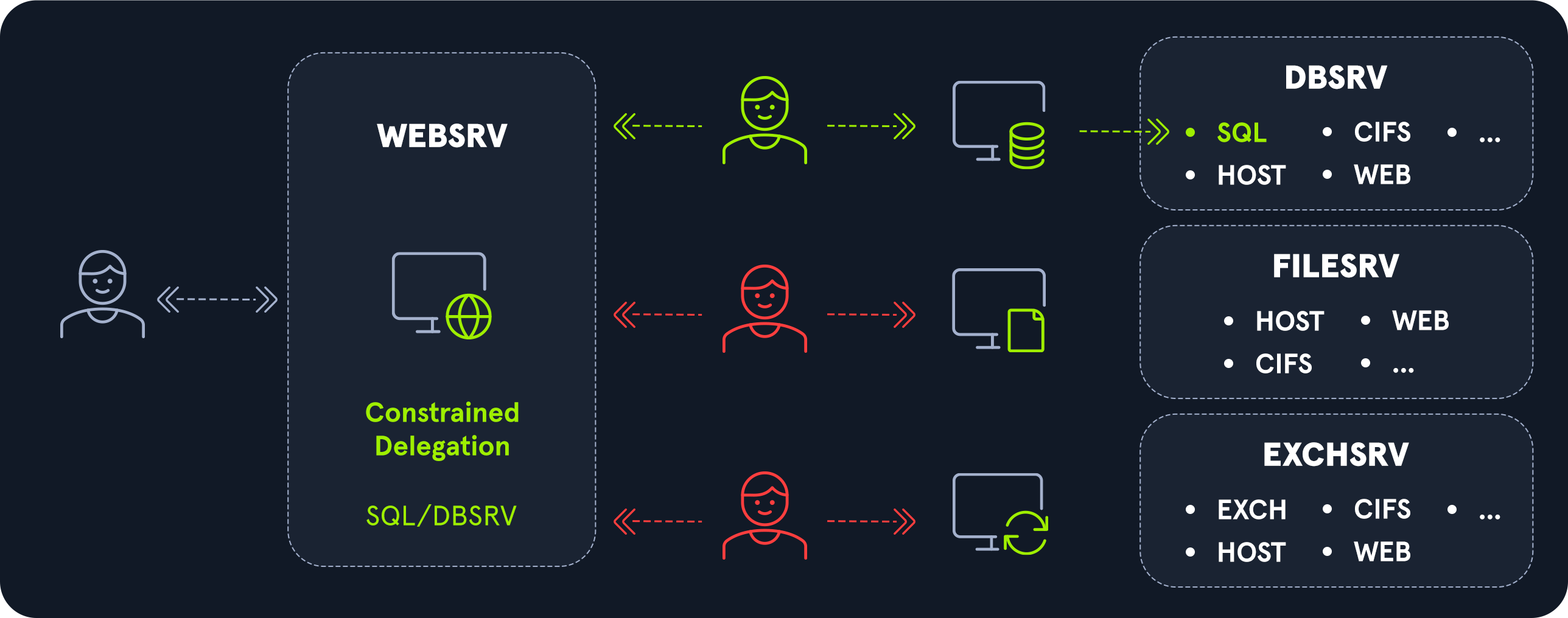
Constrained delegation is a “more restrictive” version of unconstrained delegation. In this case, a service has the right to impersonate a user to a well-defined list of services.
A constrained delegation can be configured in the same place as an unconstrained delegation in the Delegation tab of the service account. The “trust this computer for delegation to specified services only” option should be chosen.
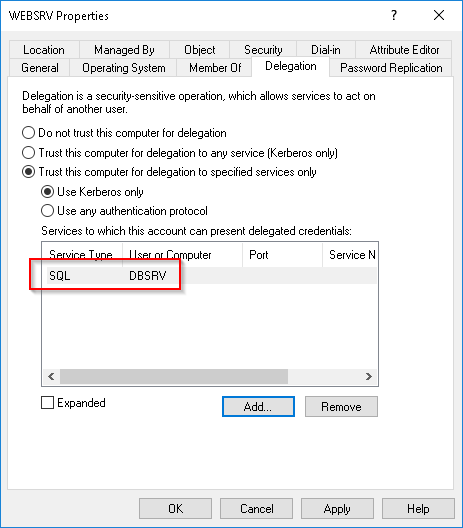
As with unconstrained delegation, this option is not modifiable by default by a service account. When this option is enabled, the list of services allowed for delegation is stored in the msDS-AllowedToDelegateTo attribute of the service account in charge of the delegation.
5. Resource-based constrained delegation
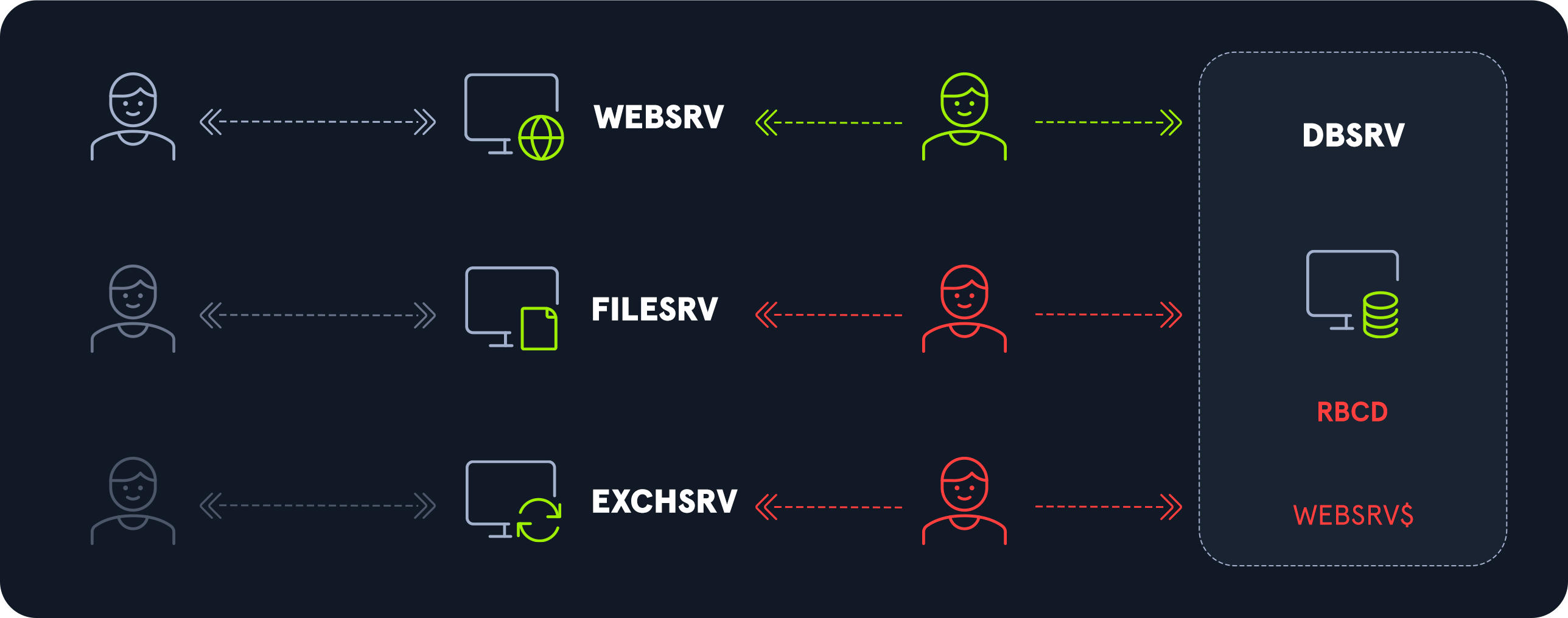
Resource-based constrained delegation reverses the responsibilities and shifts delegation management to the final resource. It is no longer at the service level that we list the resources to which we can delegate, but at the resource level, a trust list is established.
Any account on this trusted list has the right to delegate authentication to access the resource.
Unlike the other two types of delegation, the resource has the right to modify its own trusted list. Therefore, any service account has the right to modify its trusted list to allow one or more accounts to delegate authentication to themselves.
Ticket abuse
The goal of ticket abuse attacks is to steal Ticket Granting Tickets or Ticket Granting Services (TGS’) from a particular user.
There are three main ticket attacks: Golden Ticket, Silver Ticket, and Pass-the-Ticket.
6. Golden Ticket
The Golden Ticket attack enables attackers to forge and sign TGTs using the krbtgt account's password hash. When these tickets get presented to an AD server, the information within them will not be checked at all and will be considered valid due to being signed with krbtgt account's password hash.
By forging a Golden Ticket, you can impersonate a sensitive user, who has privileged access, making it a highly dangerous vulnerability.
7. Silver Ticket
A Silver Ticket is less powerful than the Golden one as it can only access the single machine it’s performed on. This attack focuses on gaining TGS rather than TGT.
One issue with the Golden Ticket attack is that when creating a TGT, the attacker needs to approach the Domain Controller to have it generate a TGS ticket before they can access any machines. This creates a unique audit record that can be identified as abnormal.
When forging a TGS ticket, the attacker can bypass the Domain Controller and go straight to the target, minimizing the number of logs left behind.
8. Pass-the-Ticket
A Pass-the-Ticket attack focuses on lateral movement, stealing the TGT or TGS.
Windows attack & defense course

-
Interactive training on the most commonly abused and fruitful attacks against Active Directory, allowing horizontal and vertical privilege escalations as well as lateral movement.
-
Learn different prevention techniques, detection methods, and how to implement honeypots (if possible) to trap attackers executing various attacks.
-
Finish the course with a practical hands-on skills assessment to test your newly developed skills.
How to mitigate Kerberos attacks
We can harden our organization’s environment against these common Kerberos attacks. Here are some common mitigations you can quickly implement:
-
AS-REP Hardening: Don't set users with Kerberos pre-authentication disabled, and protect accounts with strong passwords.
-
Kerberoasting: use long and complex passwords whilst limiting privileges of serviced accounts.
-
Delegation abuse: disable unconstrained delegation and place users into the Protected Users Group where possible.
-
Golden ticket: limit the number of admin accounts and utilize Multi-factor authentication.
-
Silver ticket: ensure service accounts have strong passwords with a complexity of 25 or more characters and rotate regularly.
-
Pass-the-Ticket: closely monitor events and check any users requesting new TGTs or TGSs outside of normal operations.
Learn how to perform (& defend against) Kerberos attacks
With Kerberos being the default authentication protocol, we must know how to test for vulnerabilities and execute these common attacks.
Our Academy module provides an in-depth study of the Kerberos protocol and its authentication process within an Active Directory network. Practice the most common attacks and upskill so you can protect the authentication process.
|
Author bio: Dimitrios Bougioukas (Dimitris), Senior Director of IT Security Training Services, Hack The Box Dimitrios has extensive experience in upskilling the IT security teams of Fortune 100/500 tech companies and government organizations. He enjoys analyzing the threat landscape as well as interpreting market and data analytics to assist Hack The Box in devising its training strategy and roadmaps, from go-to-market all the way to the syllabus level. Prior to Hack The Box, Dimitrios directed the development of training and certifications through eLearnSecurity/INE and was behind certifications like eCPTX, eWPT, and eCIR. You can connect with him on LinkedIn here. |














