Blue Teaming
5 essential Windows event log analysis tools for blue teamers
Windows event logs are the gateway to understanding suspicious activity, making these event log analysis tools essential for beginner blue teamers.

sebh24,
May 23
2024

This post is based on the Hack The Box (HTB) Academy module on Windows Event Logs & Finding Evil. The module equips learners with the skills to investigate event logs for detecting and analyzing malicious behavior.
You can learn more by browsing the catalog of free or advanced cybersecurity courses on the HTB Academy!
What are event log analysis tools?
Windows event logs are a record of events that have occurred on a computer running the Windows OS.
They include information about the system, applications running on it, providers, services, and more.
Event log analysis tools are software that gather and study log data from different sources like servers, network devices, and applications. They come with features like watching logs in real time, sending alerts, and visualizing data.
Specialized log analysis tools can automate the process, analyzing logs without the need to comb through them manually, making the analysis process faster and easier.
Master Windows event log analysis with HTB Academy

-
Gain practical skills for investigating Windows event logs to uncover potential security breaches.
-
Learn the process of installing or updating Sysmon and present real-world examples of detection, including identifying DLL hijacking, unmanaged PowerShell/C-Sharp injection, and credential dumping.
-
Delve into Event Tracing for Windows (ETW) and its architecture, learn its components, and how to interact with it.
Why do we analyze Windows event logs?
Many organizations use log analysis tools for security purposes and compliance. They provide insights into user activity and can help detect any potential security breaches, such as attempted hacks.
By analyzing these logs, we can build a timeline of what happened and even spot weaknesses in our systems. This is a valuable tool for all blue teamers to better understand system weaknesses and how to prevent them.
💡Recommended read: Decoding Windows event logs: A definitive guide for incident responders.
The benefits of using event log analysis tools
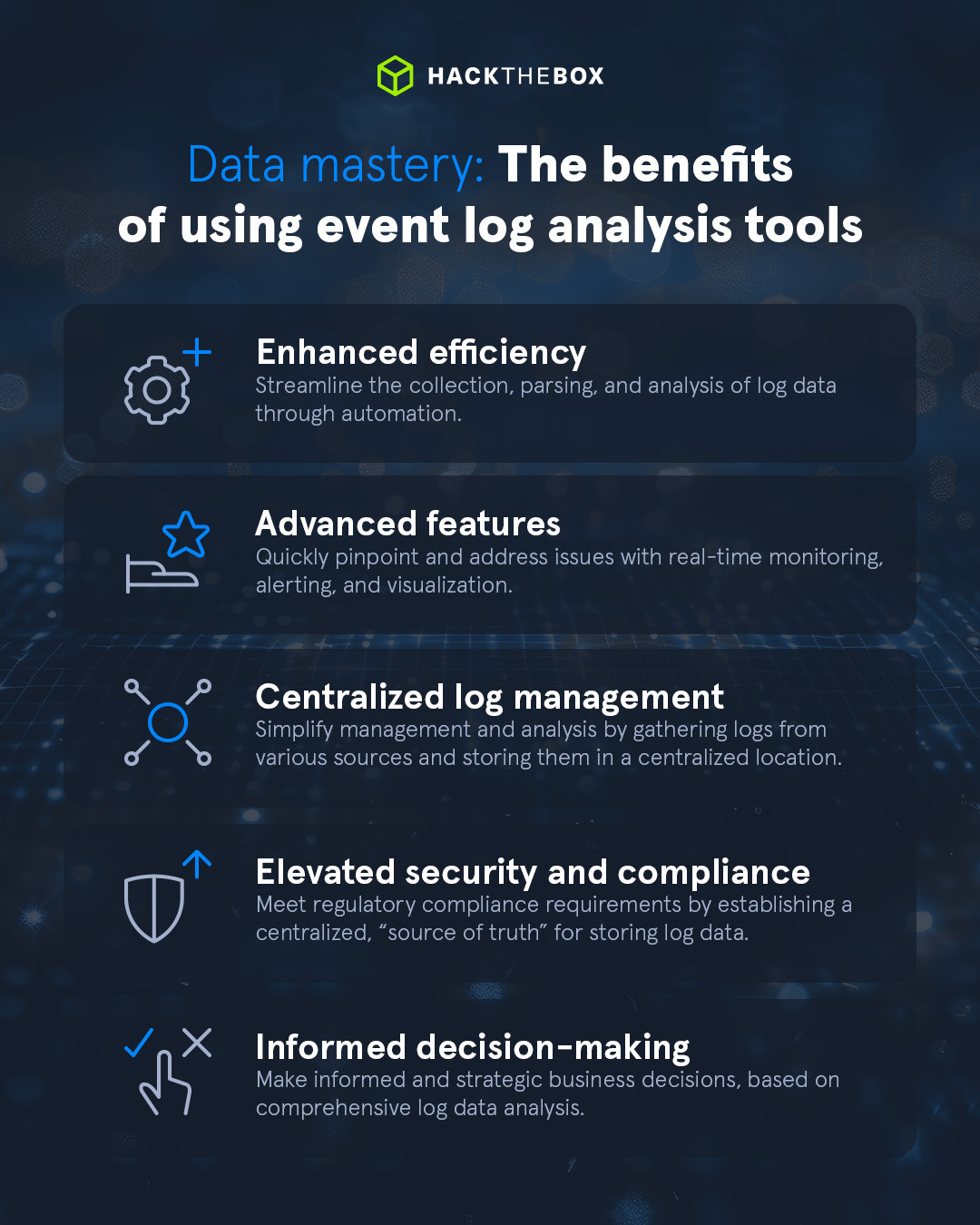
Tools can make your job much easier and be a powerful aid when spotting suspicious activity in event logs. There are potentially hundreds of thousands of event logs to shift through, which is virtually impossible to do manually.
Here are some more key benefits:
-
Reduces manual analysis workload: Streamlines the collection, parsing, and analysis of log data through automation, saving more time than manual processes.
-
Advanced features: Capabilities such as real-time monitoring, alerting, and visualization make it easier to pinpoint and address issues, enhance security measures, and optimize overall system performance.
-
Elevated security and compliance: Identify security incidents, including attempted breaches or unauthorized access to sensitive data, and utilize this information to fortify security measures. Log analysis tools will also play a crucial role in meeting regulatory compliance requirements by establishing a centralized hub for storing log data.
-
Informed security decision-making: Extract valuable insights that inform security decisions.
But we must not fully surrender to tools and allow them to do our jobs for us. Cybersecurity professionals should master the thought processes and techniques behind the tools.
Human intuition might tell you more about a vulnerability than a tool could.
You must always read between the lines, for example, a log analysis tool might not alert you of eventID 4624 (successful logon), but if this logon happened at a strange time of day, your intuition might ring alarm bells to dig a little deeper.
💡Recommended read: 7 powerful pentesting tools (& why you should stop pedestalizing them).
5 essential Windows event log analysis tools (+1 bonus tool)
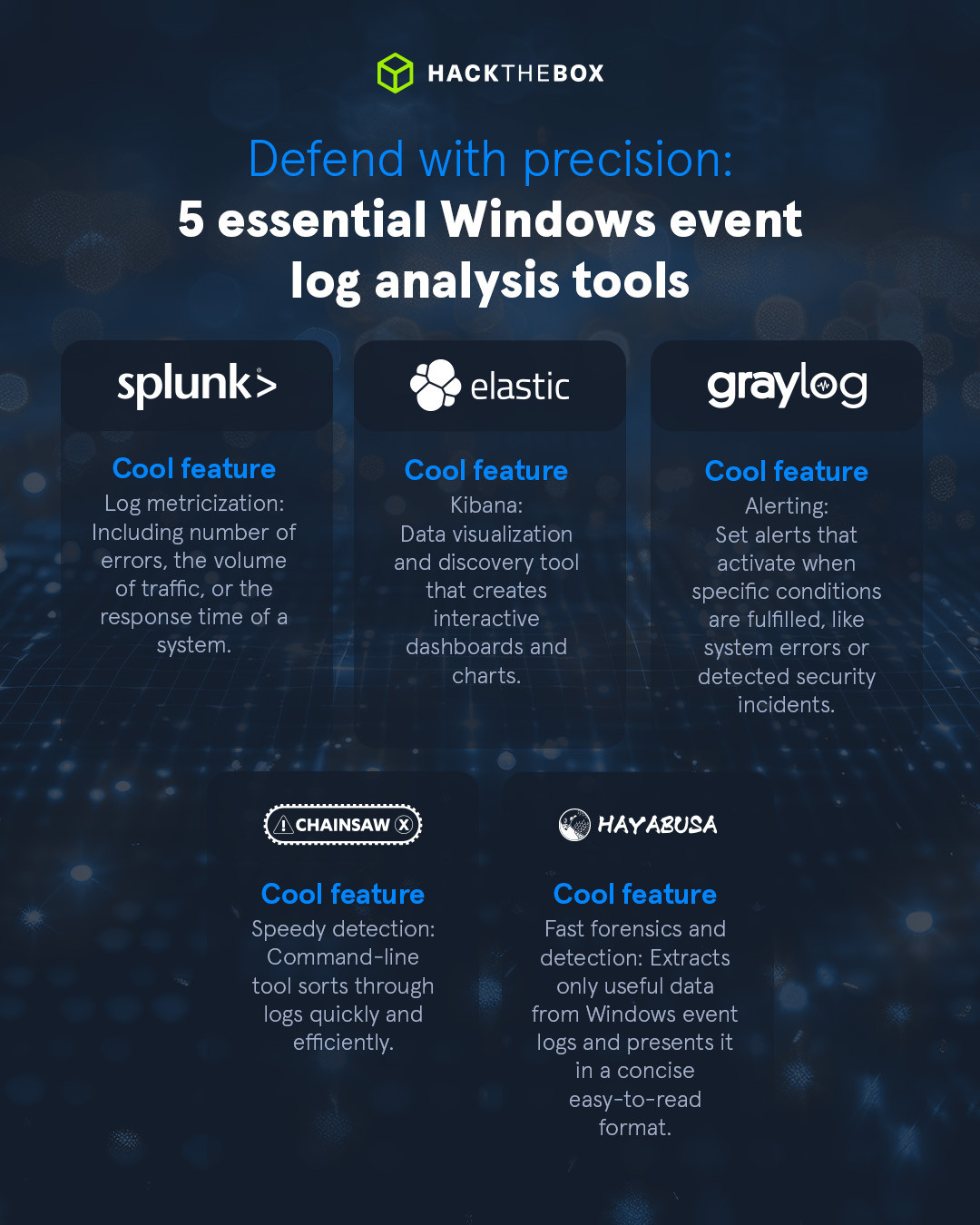
There’s a seemingly endless pool of event log analysis tools out there. Which ones should you prioritize learning as blue teamer?
We’re here to narrow down your search with five essential tools to help you analyze, identify, and respond to security incidents.
The following log analysis tools specialize in security. Use them for real-time security log analysis and post-incident forensic analysis.
1. Splunk
Splunk is a data analytics software solution known for its ability to ingest, index, analyze, and visualize massive amounts of machine data. It can drive a wide range of initiatives, encompassing cybersecurity, compliance, data pipelines, IT monitoring, observability, as well as overall IT and business management.
When it comes to cybersecurity, Splunk can play a crucial role as a log management solution, but its true value lies in its analytics-driven Security Information and Event Management (SIEM) capabilities.
Key features:
-
Timeline: Analyze log data over a specific period. This enables you to identify patterns, trends, anomalies, and track improvements. Reflecting your system’s health.
-
Log metricization: Report on performance and operational metrics calculated from log data, such as the number of errors, the volume of traffic, or the response time of a system.
-
Aggregate logs to groups and fields: Generate statistics such as totals and averages across related logs, helping to visualize problems.
-
Logging rules: Assign log rules in Splunk, such as unlimited records and search time limits.
🔎 Example Search:
Let's say, for example, we want to parse based on successful logins utilizing RDP and table it out with the time, user, and source IP:
index=winevt EventId=4624 Channel=Security LogonType=10 | table time, user, src_ipLearn how to investigate event logs with Splunk on HTB Academy

-
Learn to investigate with Splunk as a SIEM tool and develop TTP-driven and analytics-driven SPL searches for enhanced threat detection and response.
-
Discover how to identify and understand the ingested data and available fields within Splunk, through hands-on exercises.
-
Gain practical experience leveraging Splunk's powerful features for security monitoring and incident investigation.
2. Elastic
The Elastic Stack, created by Elastic, is an open-source collection of mainly three applications: Elasticsearch, Logstash, and Kibana.
The apps combine to offer users comprehensive search and visualization capabilities for real-time analysis and exploration of log file sources.
For example, an analyst could use Elasticsearch and Logstash to collect log data from servers, applications, and network devices, and then use Kibana to create dashboards and charts that show the performance and usage of the system over time.
Specific events, patterns, and anomalies can then be identified.
Key features:
-
Elasticsearch: Index, search, and analyze large volumes of data in real-time with this scalable search and analytics engine.
-
Logstash: Collect log data from various sources and send it to Elasticsearch for storage and analysis.
-
Kibana: Create interactive dashboards and charts to explore and analyze data stored in Elasticsearch.
🔎 Example Search:
event_id:4624 AND log_name:Security AND logon_type:10Discover how to use the Elastic Stack for security monitoring

-
Explore the application of the MITRE ATT&CK framework within SOCs.
-
Dive into SIEM (KQL) query development.
-
Learn how to develop SIEM use cases and visualizations using the Elastic Stack.
-
Discover how to develop SIEM use cases and visualizations using the Elastic Stack.
3. Graylog
Graylog is an open-source platform for log analysis and management that enables organizations to gather, store, and analyze log data from diverse sources.
Engineered to be scalable, secure, and user-friendly, Graylog offers many features for log analysis, visualization, and reporting.
Key features:
-
Data collection: Collect data from servers, network devices, and applications. You can configure Graylog to collect log data in real-time or on a scheduled basis, storing it in a centralized location.
-
Data parsing: Extract data from logs such as timestamps, log levels, and log messages. This can then be used for advanced search and analysis.
-
Visualization: Graphs, charts, and tables, enable users to examine and interpret log data. (Great for explaining incidents to a non-technical audience.)
-
Alerting: Set alerts that activate when specific conditions are fulfilled, like system errors or detected security incidents. These alerts can send notifications through email, SMS, or alternative methods.
-
Security: Use security tools such as role-based access control, encrypted data storage, and secure communication protocols. These measures guarantee the protection of log data, restricting access solely to authorized users.
🔎 Example search:
EventID:4624 AND Channel:Security AND LogonType:10
| table timestamp, user, src_ip4. Chainsaw
Chainsaw is a tool designed for blue teams to quickly identify threats within event logs.
Being a command-line tool, Chainsaw can be a faster method of detecting and highlighting suspicious entries on event logs. It operates using the Sigma rule (--sigma) to detect malicious activity.
Key features:
-
Search: Event logs by event ID, keyword, and regex patterns.
-
Speedy detection: Command-line tool sorts through logs.
-
Detection features: Key event logs being cleared, or the event log service being stopped. Users being created or added to sensitive user groups.
-
Compatible: Sigma rule detection against a wide variety of Windows event IDs.
🔎 Example Search:
chainsaw hunt <path_to_evtx_files> --event-id 4624 --filter 'Event.System.Channel == "Security" and Event.EventData.LogonType == 10' --columns 'Event.System.TimeCreated.SystemTime, Event.EventData.SubjectUserName, Event.EventData.IpAddress'Learn Chainsaw for digital forensics

-
Foundational forensics: Acquaint yourself with the core concepts of digital forensics, understanding its significance in today's interconnected world.
-
Memory forensics: Dive into the intricacies of volatile memory analysis. Extract, analyze, and interpret artifacts that offer invaluable insights into a system's operations and potential compromises.
-
Timeline analysis: Create chronological timelines using diverse data sources like disk images, MFT (Master File Table), USN (Update Sequence Number) journal, Windows event logs, and many more.
5. Hayabusa
Hayabusa is a Windows event log analysis tool designed by the Yamato Security group in Japan.
Hayabusa can be run either on single-running systems for live analysis, by gathering logs from single or multiple systems for offline analysis, or by running with Velociraptor for enterprise-wide threat hunting and incident response.
Key features:
-
Fast forensics and detection: Extract only useful data from Windows event logs and present them in a concise, easy-to-read format.
-
Timelines: Create single, easy-to-analyze timelines for forensic investigations and incident response.
-
Customizable: Create a list of unique pivot keywords to quickly identify abnormal users, hostnames, processes, etc.
-
Event ID metrics: Get a picture of what types of events there are and for tuning your log settings.
🔎 Example Search:
hayabusa -i <path_to_evtx_files> -e 4624 --filter 'Channel == "Security" and LogonType == 10' --output-fields 'time,user,src_ip'💡Bonus tool: A good knowledge of Windows
Microsoft Active Directory (AD) has been, for the past 20+ years, the leading enterprise domain management suite, providing identity and access management, centralized domain administration, authentication, and much more.
Throughout those years, the more integrated our applications and data have become with AD, the more exposed to a large-scale compromise we have become.
Tools, while useful, won’t solve all your problems! A strong understanding of Windows is an essential foundation.
Want to learn more about Windows? Our Windows Attacks & Defense Academy module has you covered.
Learn log analysis with HTB Academy
Windows event log analysis is a timely process when done without tools. It takes time to gather the logs and even longer to identify malicious activity. However, doing so is essential to be both compliant and proactive with your security.
Event logs can tell a story of exactly what happened, when, and why. They are a goldmine of lessons and can help analysts stop suspicious activity before it escalates.
While these tools can make your life easier and more efficient, no professional should ever just rely on tools. Always ensure you understand what you’re looking for and what different logs mean. So if a tool were to fail, you’ll be able to stand on your own two feet.
Want to learn more about event log analysis and the tools mentioned? Browse these blogs and Academy modules:














