Blue Teaming
A step-by-step guide to crafting an incident response plan
Incident response plans lay the foundations for a defensive team’s actions in the face of an incident, making them essential for speedy and effective response.

sebh24,
May 31
2024
Table of Contents
This post is based on the Hack The Box (HTB) Academy modules on Security Incident Reporting and Incident Handling Processes. These modules equip learners with the skills to accurately identify, categorize, and document security incidents, emphasizing real-world applications and best practices.
You can learn more by browsing the catalog of free or advanced cybersecurity courses on the HTB Academy!
What’s an incident response plan?
An incident response plan acts as a set of instructions on detecting, responding to, and limiting a cybersecurity incident's impact. The incident response plan should provide clear guidelines for responding to multiple potential scenarios, including data breaches, DoS or DDoS attacks, firewall breaches, malware outbreaks, insider threats, data loss, and other security breaches.
This plan also acts as a checklist of the roles and responsibilities of an incident response team in the event of a security breach. This way, everyone knows what their job is when an incident occurs.
An incident response plan covers four main areas:
-
Preparation: Before the incident, plan how your teams will respond.
-
Detection and analysis: What tools and techniques do we use to find the root cause?
-
Containment, eradication, and recovery: What caused the incident, and how do we prevent it from going further? How do we fix this incident and prevent the next?
-
Post-incident activity: How can we do better next time?
We will talk more about each of these steps later in this post.

Incident response plans should adapt to your organization as different structures and regulations apply.
Why is an incident response plan important?
To respond to an incident quickly and effectively, you need an incident response plan in place.
The goal of incident response plans is to reduce the severity of an event and protect an organization as best as possible. An effective incident response plan can yield the following benefits:
-
Faster incident response time: Spot the early signs of an incident or attack, and use the right protocols to rectify any damage quickly.
-
Early threat mitigation: Speed up forensic analysis and mitigate the impact of unplanned events with a detailed plan.
-
Better communication: Tell everyone what their responsibilities are, making it quick and simple to communicate the next steps.
-
Regulatory compliance: Many regulatory bodies require that an incident response plan is in place.
Part of the post-incident activity includes generating a report about the incident, which contains information about what caused the incident and what steps your team took to remediate it.
How do you report on an incident?
An incident response report encompasses the process by which an organization handles a breach. It aims to quickly identify an attack, minimize damage, contain, and remediate the cause to reduce the risk of future incidents.
Beyond that, incident response reports act as a conduit between identifying and remediating threats. They serve to archive past incidents, providing an invaluable source of lessons learned from previous mistakes. The lessons can be seamlessly integrated into a broader strategy for preempting and mitigating future threats.
Incident response reports should be integrated into your response planning process, which we will cover in more detail below.
💡Recommended read: How to write an incident response report
Learn how security incident reporting works

Our Academy module on Security Incident Reporting teaches teams everything they need to know about documenting and reporting an incident.
-
Explore the art of identifying and classifying security incidents.
-
Understand the systematic process of incident documentation.
-
Perfect communication strategies during incidents.
-
Dive into the critical components of a detailed incident report.
-
Analyze a real-world incident report following best practices.
How to implement an incident response plan in your organization

Now you know what an incident response plan looks like, how can you implement it in your organization? All cybersecurity teams must have a plan in place, and implementing it correctly is a crucial first step.
1. Preparation
Before any plan is put into action, you need to take stock of your current situation to lay the foundation for a successful incident response plan.
This involves ensuring that your incident response team is properly trained, that communications know what to do in an event, and employees receive basic cybersecurity training.
You could also conduct incident drill scenarios using tabletop exercises (TTX) and Capture the Flag (CTF) events to test your team’s capabilities. This helps to relieve stress, demonstrating everyone’s role before a breach happens.
Prepare for incidents with Hack The Box CTFs

-
Build your own CTF: More than 55 challenges and curated packs relevant to your team’s needs.
-
User progress report: Straightforward graphs will help you gain a better understanding of your team’s performance.
-
Benchmark: CTFs enable you to gain an overview of your team’s weaknesses, and plan upskilling initiatives in these areas.
2. Create the plan
You can then develop the incident response plan, based on our template later on. This may be done from scratch or improve upon an existing plan that’s already in place.
This document will serve as your incident responder's bible, and so much be approved by senior executives and shared with the relevant teams.
A senior leader should own this policy, making them the go-to for decision-making and communications.
3. Define responsibilities
Now’s the time to form your A-team of incident responders.
There are the essentials for an effective incident response team:
|
Role |
Responsibilities |
|
Incident lead |
This person oversees the entire incident response process, makes decisions, manages resources, communicates with executives, and sets goals. |
|
Engineers |
These are your technical wizards who identify, analyze, contain, eradicate, and recover from the incident, using the appropriate tools and techniques. |
|
Communication coordinator |
This individual is responsible for ensuring clear and timely communication both internally and externally. |
|
Executive |
This is someone from the executive team on board who can be gone to if decisions need to be made that significantly impact business. |
|
Legal advisor |
Legal advisors are required in some large incidents, so it’s key to have someone available should legal actions need to be taken. |
If your organization doesn’t have all of these team members on board, you must make the case for an effective incident response team. Not only it is a huge risk to the business not to have one, but it can impact financial and reputational aspects too.
4. Develop playbooks
Playbooks are a sequence of events and frameworks for how incident responders should act in different scenarios. For example, when an employee’s laptop is stolen, the playbook should contain the following steps:
-
Issue a remote command to wipe the device.
-
Verify whether the laptop was encrypted.
-
File a report.
-
Issue the employee with a replacement.
These playbooks should be baked into your incident response plan, enabling your team to prioritize and act quickly, preventing wrong steps from being taken or an overreaction.
Create as many playbooks as you think may be relevant. Consider also making a generalized playbook to cover incidents that don't fit under another playbook.
Test. Measure. Improve. Repeat.
5. Create a communication plan
Your communication coordinator should be responsible for drawing up a communication plan for internal teams, external stakeholders, customers, and legal entities.
This plan should define what steps need to be taken, depending on the severity of the incident and who has been impacted. This is vital for preventing misinformation from being spread and making the right people aware.
6. Test and update the plan
Now your plan is ready to be put to the test! You don’t need to wait for an incident, you can recreate your previous incident TTX, and see how the new plan has strengthened the process.
Then, when a real incident occurs, your incident response team should follow the plan and report on any areas of weakness.
The more incidents (and TTXes) that occur, the better your plan will become, with lessons being learned every time.
Incident response plan template
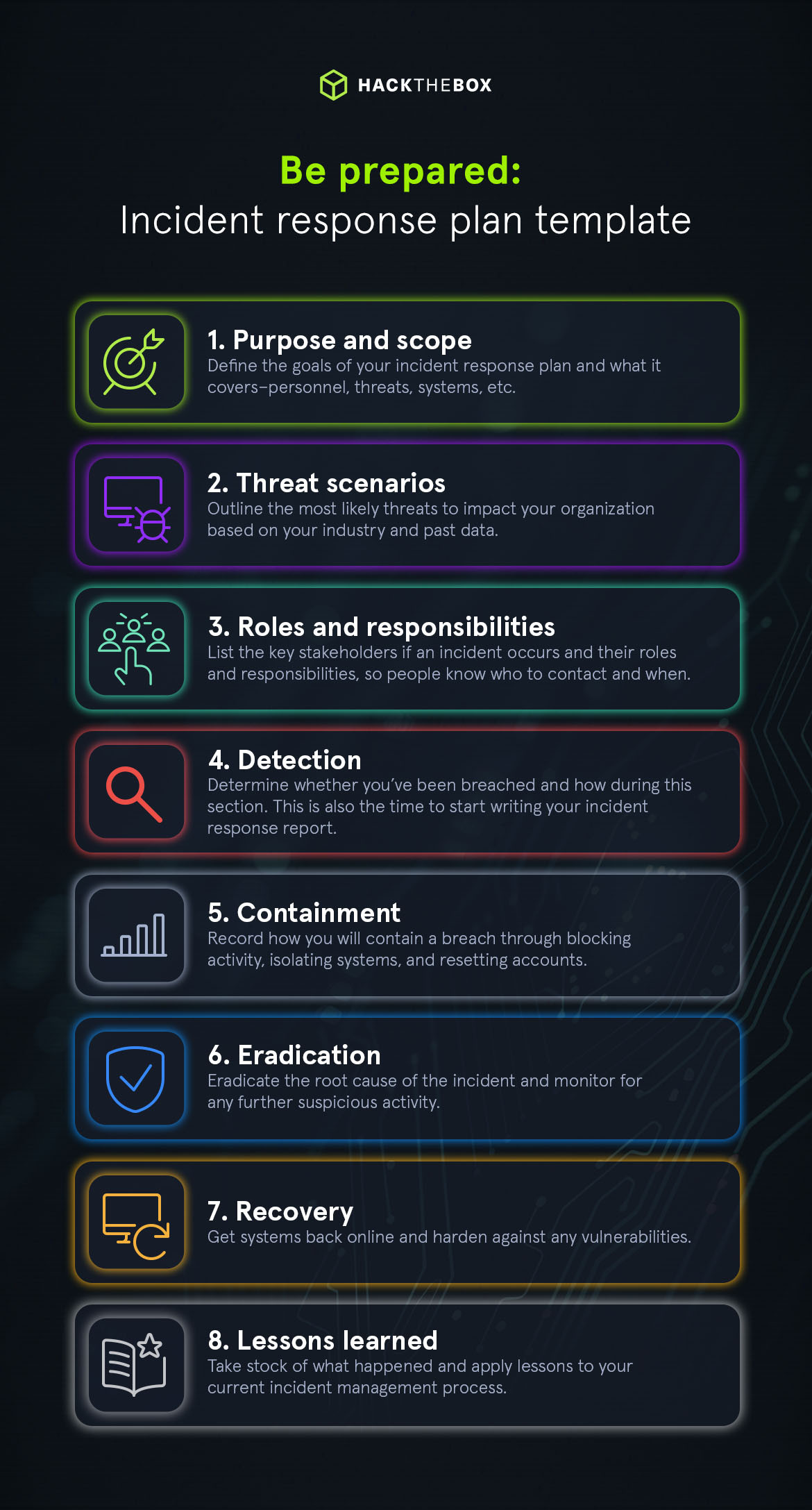
Incident response plans should flex to your organization, but below are some key elements that you should use as a template to structure your plans and documentation.
1. Purpose and scope
The very first section of your incident response plan should define why the plan is in place and the extent of its coverage.
The scope defines the types of incidents that the plan covers, the systems and data included, and the personnel who are part of the plan.
Some of the written policies and documentation should contain an up-to-date version of the following information:
-
Contact information and roles of the incident handling team members, and alternates.
-
Contact information for the legal and compliance department, management team, IT support, communications and media relations department, law enforcement, internet service providers, facility management, and external incident response team.
-
Network diagrams.
-
Organization-wide asset management database.
-
User accounts with excessive privileges.
-
Forensic/Investigative cheat sheets.
2. Threat scenarios
Outline potential incidents that can impact your organization, Certain incidents may be more likely than others, depending on your industry.
Here are some of the most common threats that businesses face:
-
Malware.
-
Denial-of-Service (DoS) Attacks.
-
Phishing.
-
Spoofing.
-
Identity-Based Attacks.
-
Code Injection Attacks.
-
Supply Chain Attacks.
-
Insider Threats.
-
DNS Tunneling.
-
IoT-Based Attacks.
3. Roles and responsibilities
A crucial element of an incident response plan is defining the key stakeholders involved when an incident occurs. This saves a huge amount of time in the event of an incident and enables everyone in the organization to know who to go to.
The plan should also outline what responsibilities each individual has.
4. Identification
This section is what you’ll turn to to determine whether you’ve been breached and how. Some common questions to ask at this stage are:
-
When did the event happen?
-
How was it discovered?
-
Who discovered it?
-
Have any other areas been impacted?
-
What is the scope of the compromise?
-
Does it affect operations?
-
Has the source of the event been discovered?
While having documentation in place is vital, it is also important to document the incident as you investigate. Therefore, during the identification stage, you will also have to establish an effective reporting capability.
Incidents can be extremely stressful, and it becomes easy to forget this part as the incident unfolds itself, especially when you are focused and going extremely fast to solve it as soon as possible.
Try to remain calm, take notes, and ensure that these notes contain timestamps, the activity performed, the result of it, and who did it. Overall, you should seek answers to who, what, when, where, why, and how.
5. Containment
Here, you’ll outline the containment process. Rather than acting rashly and deleting content to remove the breach, it’s best to contain and isolate, so you can identify what caused the incident to happen in the first place. This usually includes blocking activity, isolating systems, and resetting accounts.
Short and long-term containment strategies should be put in place, including system back-ups so business operations can be quickly restored.
Some common questions to ask at this stage include:
-
What’s been done to contain the breach?
-
Has any malware been discovered or quarantined?
-
What sort of backups are in place?
-
Does your remote access require true multi-factor authentication (MFA)?
-
Have all access credentials been reviewed?
-
Have you applied all recent security patches and updates?
6. Eradication
Now’s the time to eradicate the root cause of the incident. This often requires similar actions to containment, such as blocking, hardening, and patching systems.
It’s important to set time aside to monitor for further suspicious activity, as threat actors could bury themselves deeper in systems to avoid detection.
7. Recovery
This is the stage by which systems should have returned to “business as usual”. Systems and data should be cleaned and back online. This is also a stage where PR communications and other tactics may take place, depending on your industry and the nature of the incident.
Take any necessary extra security steps to prevent another breach, such as changing privileged access and passwords, and installing patches.
8. Lessons Learned
The final stage of your incident response plan should be to take stock of what happened and apply lessons to your current incident management process.
You should hold a meeting with the incident response team members (everyone listed in this plan), and discuss the following:
-
What worked well in your incident response plan, and what could be improved?
-
What changes need to be made to the security?
-
How should employees be trained differently?
-
What weakness did the breach exploit?
-
How will you ensure a similar breach doesn’t happen again?
Fail to prepare (for incidents), prepare to fail
Implementing, testing, and tweaking your incident response plan is essential for all blue teams. Incidents and breaches will always happen, so having a plan in place is vital to minimize the impact on business operations.
Ready to learn more? Here’s all of our essential content on incident response:
















