Cyber Teams
4 steps to implement a skill-based candidate assessment strategy
Learn how to source candidates with validated skills and successfully run threat-connected assessments on HTB Enterprise Platform.

b3rt0ll0,
Jun 28
2024
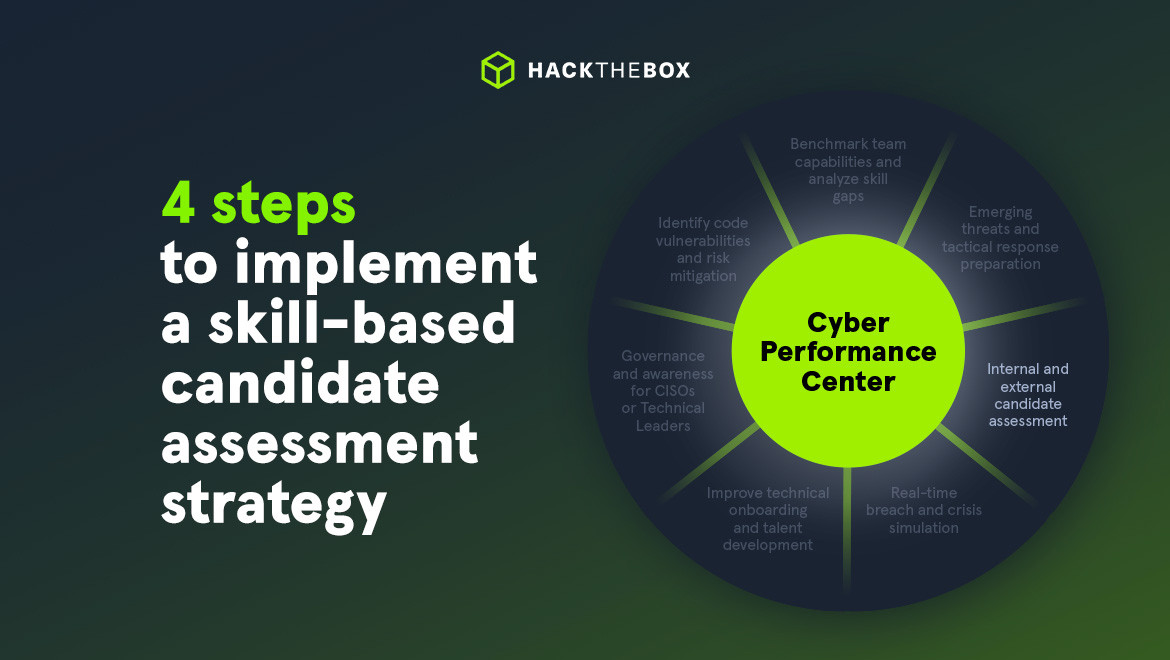
The industry doesn’t need more candidates, the industry needs more qualified candidates.
However, agreeing on what “qualified candidates” means is where the puzzle of cybersecurity recruitment gets tricky.
The cybersecurity job market has been (in)famous over the past decades for setting high expectations for entry-level applicants—like requiring expensive certifications or degrees as a mandatory requirement. This practice contributes to making security an unnecessarily tough field to enter—now a serious problem also for recruiters and CISOs Loading Preview...
And here comes the good news: the trend seems to be changing.
With the rapid evolution of the technologies and threat landscape, it is now obvious how hiring effort should be focusing on skills validation rather than a checklist of requirements.
As a confirmation, nearly half of the companies located in the United States plan to eliminate bachelor’s degree requirements in 2024 Loading Preview...
Surprisingly, the public sector is also following this direction. The Biden-Harris administration has recently communicated an overhaul of federal hiring processes, committing to become fully skills-based for a series of technical roles.
In the following paragraphs, we will go over the main challenges of sourcing candidates, how to verify skills successfully, and the practical solutions Hack The Box (HTB) offers to optimize these processes.
A look into the current cyber workforce
Learn how security and business leaders worldwide can increase team performance by hiring skilled candidates and retaining them.

Hire, assess, and retain in 2024
A skill-focused hiring approach requires advanced capabilities in talent sourcing and candidate assessment. These two practices are fundamental to fixing hiring processes that are currently not performing as expected, putting additional pressure on CISOs and technical leaders.
Additional challenges arise if we also take into consideration internal candidate assessment strategies—fostering internal mobility, reskilling, and promotions.
What are the crucial challenges companies are facing to successfully hire, assess, and retain cybersecurity talent in 2024?
Skills validation
Verifying the authenticity of claimed skills and experiences from external candidates can be challenging or unclear. Companies sometimes fall into extremes, providing extensive exercises that are demotivating the candidate, to bite-sized assessments that are not effective to evaluate the skills required.
Additionally, technical recruiters are not fully aware of what specific skills the candidate must be assessed on, making it even more difficult to identify the right fit for the team (and potentially compromising retention with unclear job descriptions or hiring expectations).
Access to talent
The high demand for cybersecurity talent creates a competitive market, making it challenging to attract and secure top external candidates.
According to ISACA Loading Preview... Loading Preview...
Limited visibility
Organizations may fall short when it comes to comprehensive visibility into the cybersecurity skills of the current workforce. Technical leaders often lack adequate skills tracking, self-assessment, feedback mechanisms, and insufficient integration with talent management systems to make data-driven decisions on staffing.

At Hack The Box, we are committed to solving these challenges and creating a more realistic hiring process with assessment strategies modeled on threat-connected requirements, skills, and knowledge that can support organizations in finding the next ideal security team member.
A solution to revolutionize cybersecurity hiring
Rethinking your cybersecurity recruitment strategy is more than just a good practice. It's a game-changer.
This is not just about adding new members to your team. It’s about transforming the very fabric of your cybersecurity workforce, elevating your team's performance, and improving security posture.
💡 Don’t miss our practical tips Loading Preview...
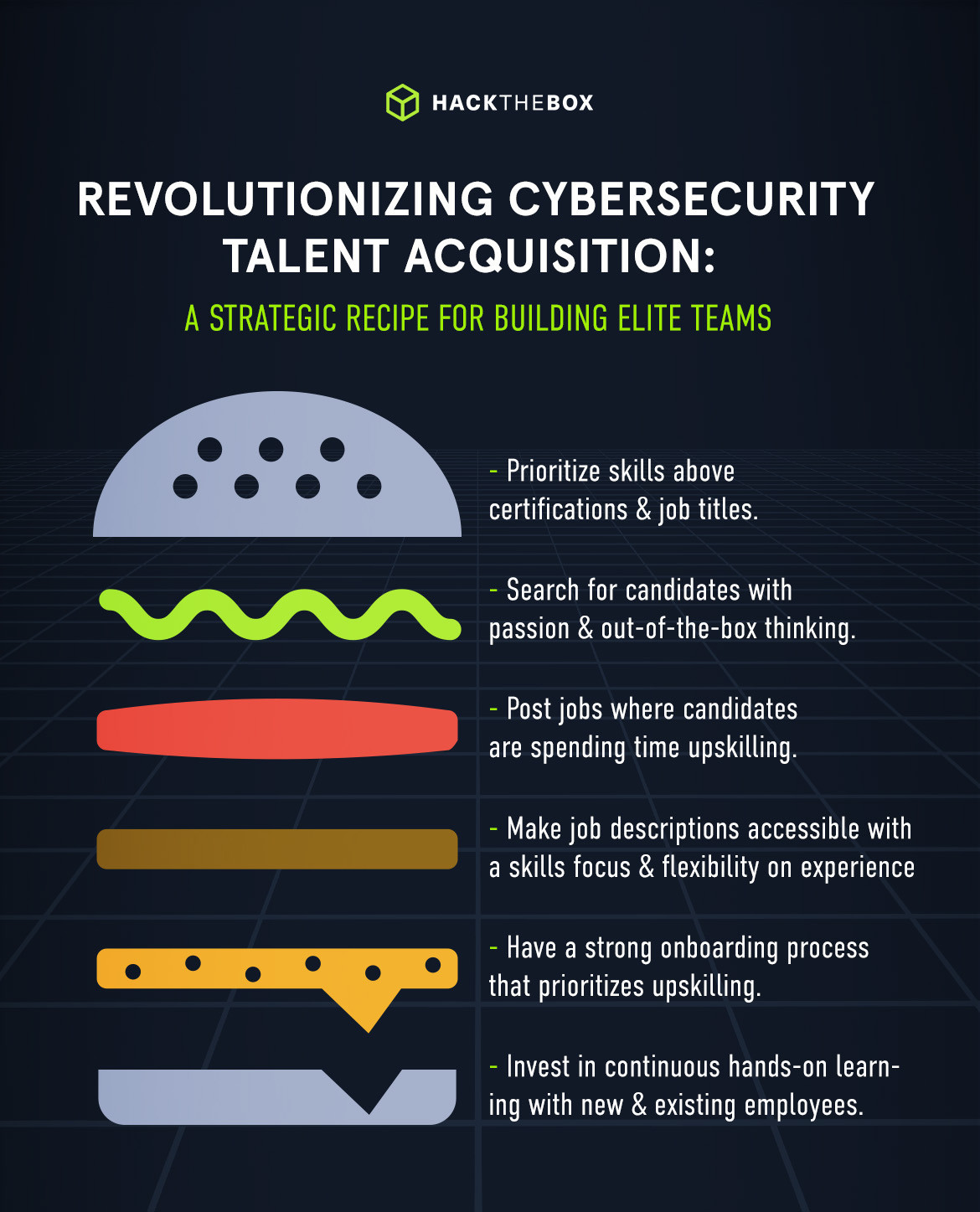
Effective hiring journeys begin at the talent mapping stage. By analyzing skills and capabilities, recruiters and technical leaders can uncover blind spots within a team and craft the entire process accordingly.
Using advanced recruitment solutions is a fundamental practice to address evolving challenges in candidate assessment. Here is how Hack The Box provides the necessary products and features to identify your next cybersecurity hire!
Step #1: Map your hiring needs
As mentioned above, the first requirement to streamline the hiring strategy is to carefully understand the skills the new candidate must possess.
Regular team assessments Loading Preview...
The CTF report can be used to map the specific knowledge domains lacking in the team, providing a data-driven and threat-connected approach to security recruitment.
Step #2: Source candidates through Talent Search
Talent Search Loading Preview...
New open job opportunities can be posted in just a couple of clicks, granting immediate access to a pool of more than 600,000+ individuals looking for a new occupation!
And not only that: the stakeholders taking part in the hiring process will be able to verify the achievements of all applicants, starting to validate their skills even before the assessment process.
Using the enhanced content categorization Loading Preview...
Step #3: Candidate assessment
Once the team has identified the perfect candidate to test, the hiring manager can set up the assessment environment.
By using Spaces Loading Preview...
-
Inviting the candidate as Guest User to the enterprise environment.
-
Select a scenario and assign it to the candidate.
-
Toggle “Mask Mode”, a feature that hides all the scenario information and restricts access to write-ups or other guided settings for maximum integrity.
As an example, if we want to assess a SOC Analyst candidate focusing on skills related to Splunk and ELK usage, hiring managers can easily search and identify the related scenarios (in this case, one of our Sherlocks defensive labs).
Step #4: Evaluation and moving forward
Once the candidate completes the assessment, the results are available on the user profile under the HTB Enterprise Platform reporting capabilities.
Managers have the opportunity to highly customize the assessment process to ensure the candidate has been tested with the right methodology. As an example:
-
Candidates can be assigned to more than one scenario, in order to test a diverse range of skills and knowledge domains. Providing more insights on the capabilities and skills matrix.
-
Hiring managers can set a time limit for candidates to access the assessment. Once they launch the scenario, they will need to complete it by the timeframe specified.
-
For further evaluation, we also suggest to require from candidates a written report about their assessment, in order to further elaborate on the logic of steps taken and demonstrate full ownership on the task.
Of course, candidate assessment practices on Hack The Box do not replace traditional recruitment strategies. However, delivering a practical assignment highly increases your chances of identifying the right candidate for your team based on data, making the entire process faster and more efficient.
The surefire way to hire talent with proven skills
It’s surely time to rethink our methodology to assess and hire the best talent, for the good of the business and the people.
“Hack The Box has been a great platform for us as a recruitment agency to quickly establish the caliber of candidates we represent for ethical hacking positions. The platform provides a credible overview of a professional's skills and ability and a ranking that clients consider when selecting the right hire. An active profile on HTB certainly strengthens a candidate's position in the job market, making them stand out from the crowd and highlighting their commitment to skill development.”
Ryan Virani, UK Team Lead @ Adeptis
Multiple business customers using Hack The Box for candidate assessments through the years have seen major improvements in the quality of hires, time reduction in the hiring process, and even optimization of financial resources allocated to the hiring budget.
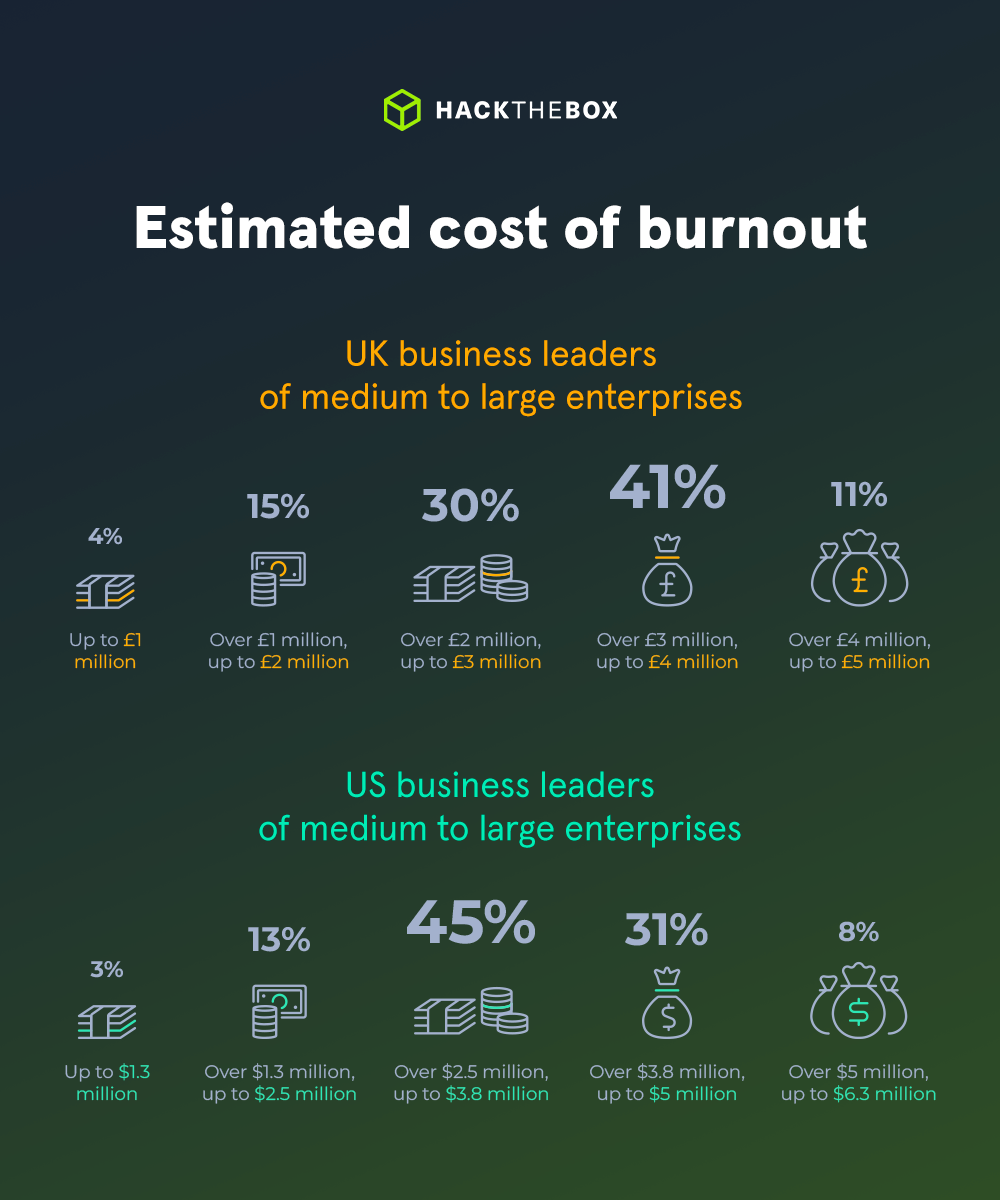
According to a recent (ISC)² report Loading Preview...
By adding this figure to our latest research on the impact (and cost) of burnout in the industry Loading Preview...
Choose HTB to boost your cyber performance
Today’s cyber threats present a new challenge to organizations, and unskilled teams pose a real risk to the security of your business. This is why cybersecurity performance programs and continuous improvement are no longer a nice-to-have, but a necessity.
Start now to lead the way into skill-based cybersecurity hiring!
-
Risk mitigation: Timely content offers training on the latest CVEs in real-world environments, reducing risk and exposure to these vulnerabilities.
-
Employee retention: Cybersecurity teams that are offered upskilling opportunities are far more engaged and less likely to burn out.
-
Performance benchmarking: Conduct CTFs and gap analysis to identify weaknesses in your security posture.
-
Tailored training to industry standards: HTB content is mapped to MITRE ATT&CK and NIST NICE frameworks so you can assess your cyber preparedness in different areas.
-
Boost organizational awareness: HTB can assess cyber readiness and performance company-wide with effective practices like tabletop exercises (TTXs) or nearly practical assessments designed for security staff and non-technical teams.














